Operating System
Theory Summary Blog Post
Describe features of contemporary operating systems and
their structures
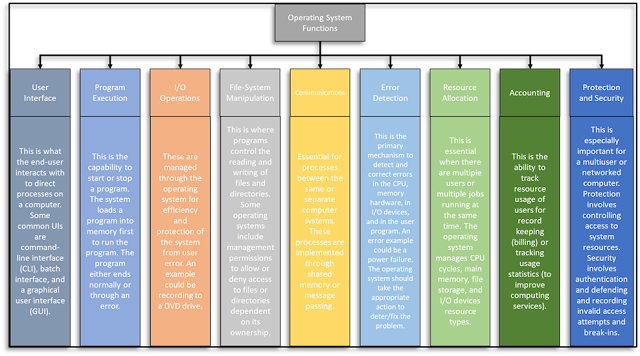
Contemporary operating systems have
extensive features guiding the user and computer system to have purposeful interactions.
Specifically, the features include the user interface (UI), program execution, input/output
(I/O) operations, file system manipulation, communications, error detection,
resource allocation, accounting, and protection and security (Silberschatz,
Galvin, & Gagne, 2014). The below concept map describes what these features
are in an operating system.
Operating systems can be structured
in many different ways, including monolithic, layered, or hybrid structures.
The monolithic structure has all the functionalities of the operating system
compiled into one space, whereas the other two approaches use a hierarchical
structure. Contemporary operating systems used layered or hybrid approaches to
prevent system vulnerabilities discovered in the archaic monolithic approach.
In these methods, the subsystems or subcomponents are referred to as modules.
The course text shows a unique example of a layered approach for the Mac OS X,
also outlined below. The layers are hierarchical, starting with the Aqua graphical
user interface (GUI), the application environments and services layer, and the
kernel environment. The kernel environment details the I/O kit, kernel
extensions, Mach (memory management support), and BSD (support for networking
and file systems) functions (Silberschatz, Galvin, & Gagne, 2014). As
outlined in the description above and the graphic below, we can see that
subsystems or subcomponents use functions and services of only lower-level
layers or modules that can call any other module, alluding to its benefit in
reducing system vulnerabilities.
Discuss how operating systems enable processes to share
and exchange information
Operating systems enable processes
to share and exchange information by utilizing what is called a thread. Threads
are split into two categories: single- and multi-threaded. In a single-threaded
model, a single process requires all of the resources necessary for execution,
whereas a multi-threaded model does not (Silberschatz, Galvin, & Gagne,
2014). In other words, the multi-threaded model uses parallelism by using
multiple threads running simultaneously and sharing resources. Consequently,
this means that a multi-threaded approach uses fewer resources due to the
threads sharing code, data, and files. The two levels of threads are user-level
and kernel-level. User-level threads are independent of kernel-level threads
and are controlled by the user, whereas the operating system controls kernel-level
threads.
Threads can be further broken down into processes, process states, and process control blocks. A process is the execution of a program and includes the program code and the current activity. A process is active, working in conjunction with a program counter to execute instructions. During the execution of instructions, the current activity of a process is defined as its state, which can be new, running, waiting, ready, or terminated (Silberschatz, Galvin, & Gagne, 2014). When the process is created, the state is new. Running, waiting, and ready correspond to instruction execution, waiting for an event to occur, and waiting to be assigned to a processor, respectively. The process control block (PCB) contains the information of the process related to it. In other words, it is the repository for any information, which can vary from process to process.
Explain how main memory and virtual memory can solve
memory management issues
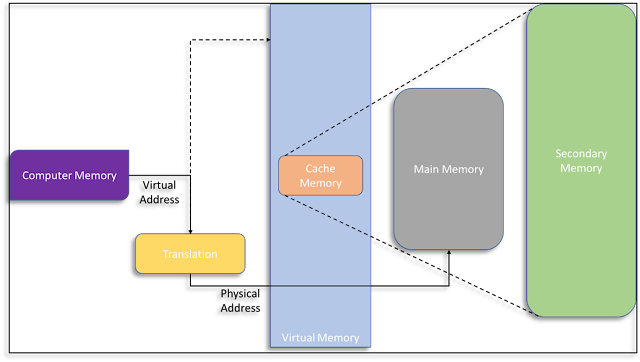
The main memory, also known as the Random
Access Memory (RAM), refers to the physical memory that is the internal memory
of a computer system. Virtual memory refers to a memory management technique in
which secondary memory is used in lieu of main memory. Virtual memory is a
common technique to solve memory management issues in a computer’s operating
system. It uses both hardware and software, enabling a computer to compensate
for physical memory shortages, temporarily transferring data from RAM to disk
storage (Silberschatz, Galvin, & Gagne, 2014). While it is beyond the scope
of this prompt, virtual memory can be either paged or segmented when
transferring data.
The virtual address generated by
the CPU during program execution allows mapping chunks of memory to disk files,
acting as if it were the main memory. The memory management unit (MMU) can map
a virtual address space to a corresponding physical address, assisting in that
mapping (Silberschatz, Galvin, & Gagne, 2014). Essentially, virtual memory
frees up RAM by swapping data that has not been used recently over to a storage
device. Consequently, this also improves system performance, multitasking, and using
robust programs.
Explain how files, mass storage, and I/O are handled in a
modern computer system
In a modern computer system, files
are handled by directory structures. There are five common directory
structures, including single-level, two-level, tree-structured, acyclic-graph,
and general graph directories. A single-level directory is the most rudimentary
structure, containing every file in a single directory. The two-level directory
is slightly more advanced, adding a master file directory above the user file
directory. The tree-structured directory applies a combination of the first two
directory structures to create several levels through subdirectories and is the
most common directory structure employed today. The acyclic-graph directory
introduces collaboration between users by sharing subdirectories in a file
system, where multiple users can create, edit, and delete files that can be
seen near-real time on each computer system. The final directory structure is
the general graph directory, which allows cycles to search a directory (Silberschatz,
Galvin, & Gagne, 2014). Examples of these structures can be seen below.
Mass storage typically refers to storing
large amounts of data on a piece of persistent (non-volatile) hardware, such as
magnetic disks, solid-state disks, or magnetic tapes. These mass storage
devices used in computer systems have their data organized in a file system.
This data is memory mapped so that it can traverse a computer system, much like
I described in the above section about virtual memory.
The most commonly known I/O devices
are user interface devices (mouse, keyboard, etc.); however, storage (CDs,
DVDs, etc.) and transmission (Bluetooth) are other common devices. Input/output
(I/O) devices are handled in modern computer systems by device drivers, which
are computer programs that tell the OS and other software how to communicate
with the hardware. The following is a list of hardware components of I/O
devices (Silberschatz, Galvin, & Gagne, 2014):
- · Bus: A group of wires that send messages via electrical signals according to a specific protocol.
- · Device controller: An electronic that controls a port, bus, or device.
- · Port: The point of connection between a device and a computer.
- · Registers: These contain data and control signals, allowing the processor and controllers to communicate. This is also the nexus for the hardware and software interface.
First, I/O devices are used to
communicate instructions (through the air or physical cables). Those
instructions initiate buses that select an I/O device which subsequently moves
bits into or out of device registers. Alternatively, device controllers can
utilize memory-mapped I/O where “…the device-control registers are mapped into
the address space of the processor” (Silberschatz, Galvin, & Gagne, 2014, Page
563). From there, the CPU executes I/O requests.
Outline the mechanisms necessary to control the access of
programs or users to the resources defined by a computer system
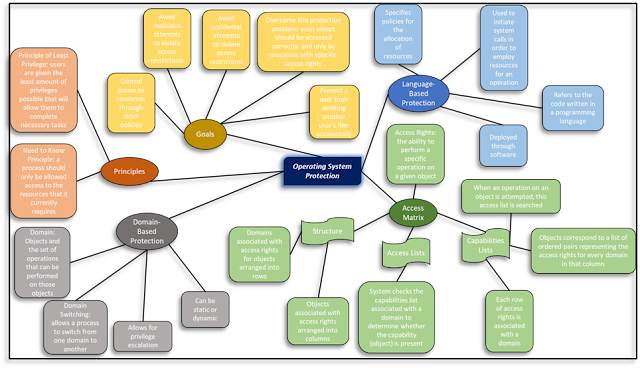
The mechanisms necessary to control
the access of programs or users to the resources defined by a computer system
can be divided into the concepts of protection and security. Protection focuses
on the internal problem of controlled access to a computer system. More so,
protection principles involve adjusting the number of privileges given to
programs, users, and systems. The principle of least privilege is a great
example of this, which reduces the amount of harm introduced to a computer
system when employed effectively (Silberschatz, Galvin, & Gagne, 2014). The
actual deployment of this mechanism is through what is called an access matrix.
The access matrix controls access rights (the ability to perform a particular
operation on a given object) and is a protection model where columns represent
objects (system resources) and rows represent domains (users) (Silberschatz,
Galvin, & Gagne, 2014). An access matrix can be implemented in two ways:
through access lists or capability lists, or a combination thereof. These lists
are further described in the concept map below.
While protection focuses on the
internal problem of controlled access to a computer system, security considers
the potential external threats. To protect against these potential threats,
security measures must be taken at four distinct levels: physical (protected
access to sites, rooms, terminals, and workstations containing the computer
systems), human (user authorization for attempted access to a system),
operating system (protection against malign or accidental security breaches),
and network (connections over private or shared lines, including leased,
internet, wireless, or dial-up) (Silberschatz, Galvin, & Gagne, 2014). Additional
measures to take to secure programs, systems, and networks are user
authentication and one-time passwords. Authentication is where the operating
system verifies the user before allowing access to a system. One-time passwords
are passwords that can only be used once, implemented through various methods
(random numbers, secret keys, network passwords, etc.).
Recommend how you will use these concepts about operating
systems theory in future courses and future jobs
Understanding the above concepts
about operating systems theory can profoundly affect academic studies and
future jobs, especially if you are seeking a technological or computer-centric
career. Due to the undoubted effects on performance and function, choosing the
right operating system is a must. In academia, understanding operating system
theory can help in selecting an OS and optimizing performance while conducting
business. For example, I may want to use a Linux-based operating system for coding
because it is fast, efficient, and lightweight.
I can use operating systems theory
in my current or future job through the conduct of my daily tasks. File system
structure is one example. By understanding the different directory structures,
I can decide where to place a document, if only to mitigate sharing the
document with users who do not have a need to know. In future positions, I may
be tasked to manage computer systems, where I will need to understand operating
systems theory. I can also use this knowledge to recommend which OSs my company
should use for specific operations. Overall, employing my knowledge of
operating systems theory can help protect, secure, and improve the performance
of company operations. How can this knowledge impact your professional and academic
careers?
Reference
Silberschatz, A., Galvin, P. B.,
& Gagne, G. (2014). Operating system concepts essentials (2nd
ed.). Retrieved from https://redshelf.com/





No comments:
Post a Comment